Dear Microsoft support team,
My name is Javier Ortega, and I am writing to seek assistance with: Authentication from .Net application to Entra tenant, with google users.
Currently we have a group of users migrated to a customer (external) entra tenant. Some of these users are gmail accounts. And we want these users to be able to authenticate, in order to access an internal web site. We have set up and added the Microsoft authentication flow on our application by calling the Microsoft authentication OpenIdConnect events and redirecting to Microsoft user authentication.
When testing the program flow, we enter a gmail account on the authentication, then the Microsoft authenticator redirects to google authentication app. And user and passwords credentials are entered, and after finishing the authentication, we get this error message:
“Account already exists
Your account 'emailabc@gmail.com' already exists. Click Next to sign in with that account.”
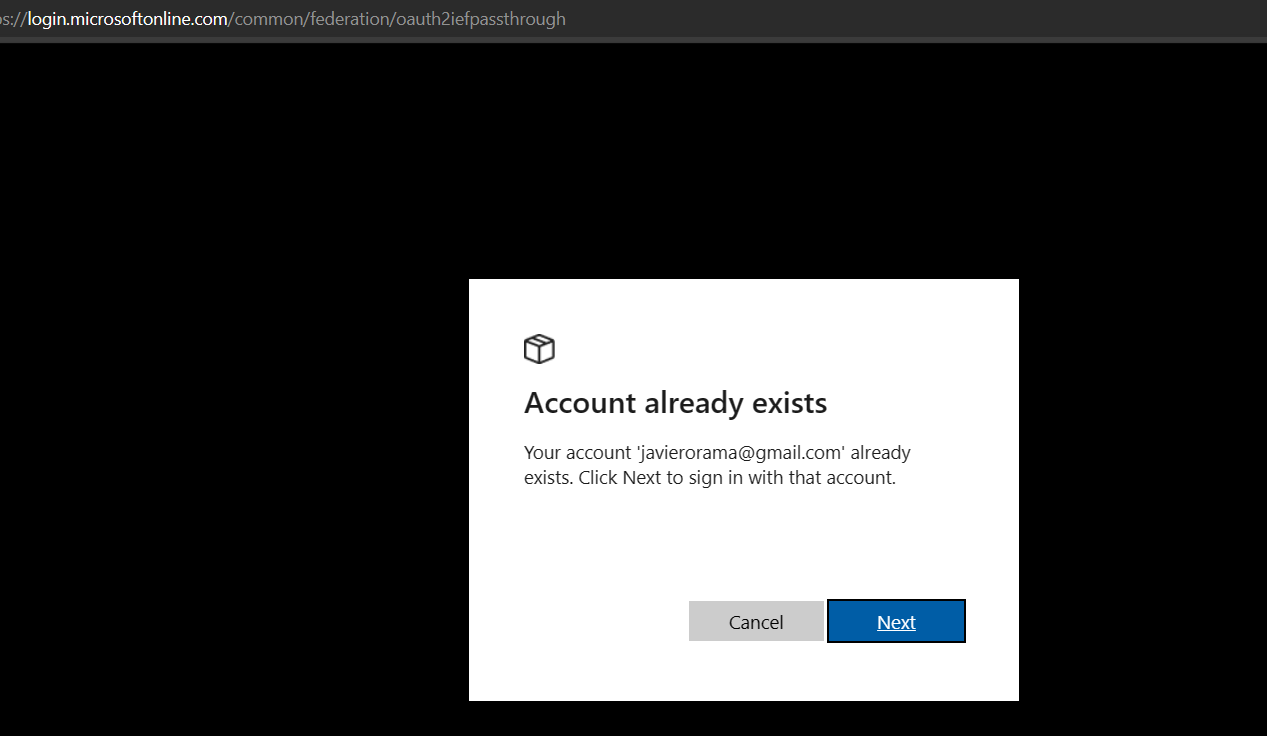
Which is preventing our gmail users from getting access to the web portal. It is occurring for all gmail users. And instead of authenticating the users and landing on our internal web site, we get this error. We do not want to create the account on our tenant, we just want those users to authenticate by entering gmail user/password.
Also when we click on the next button, we get the same error page.
We are sending the following parameters to the Microsoft authentication application:
| Parameter |
Value |
| entraTenantId |
The Guid of the tenant |
| IssuerAddress |
“https://login.microsoftonline.com/{entraTenantId}/oauth2/v2.0/authorize" |
| ClientId |
The id of the application registered on the tenant |
| ClientSecret |
The corresponding client secret. |
| Instance |
https://login.microsoftonline.com/ |
| UserFlow |
The guid of the user flow. |
|
|
On the entra configuration:
The tenant where we have the list of users is a customer tenant.
Also, we have created a multitenant application to which we have granted permission.
This is the list of permissions granted to the application:
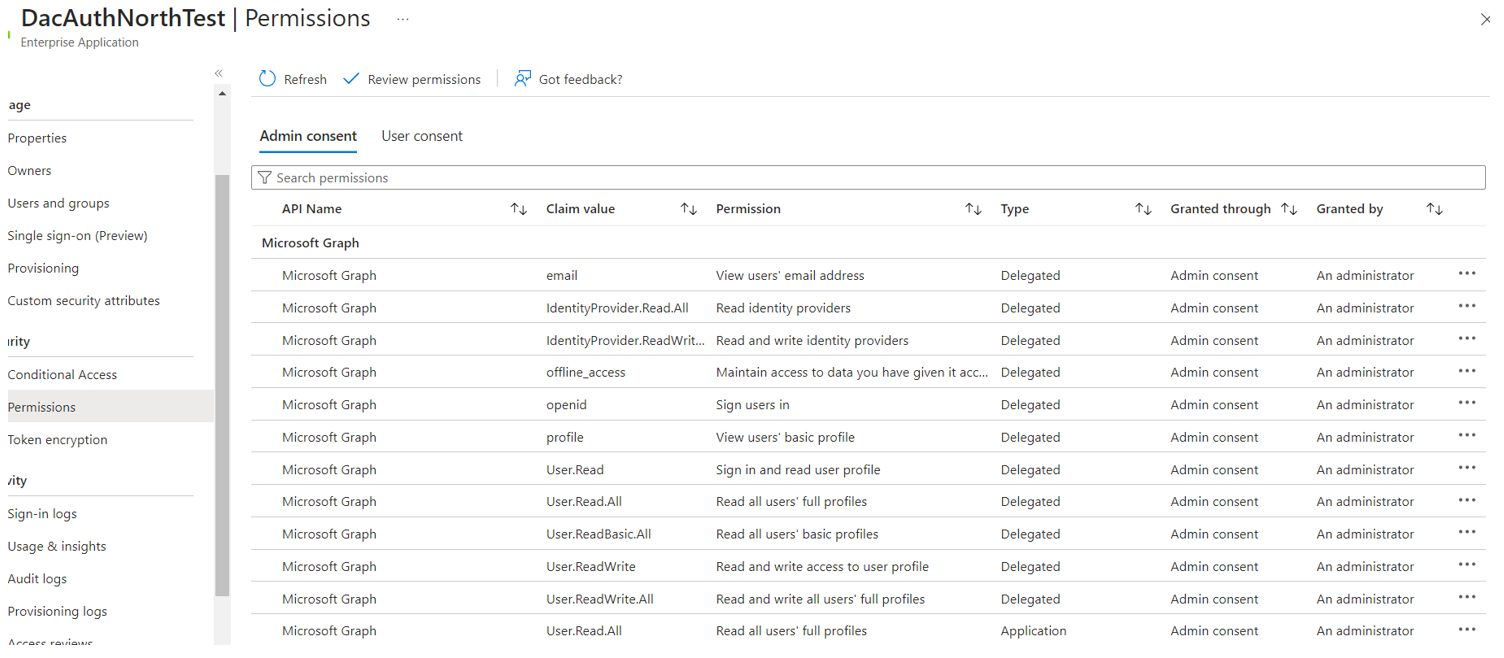
We have added Google as an identity provider on the tenant too. We follow the steps mentioned on the next link to create an application in google developer console and add google as identity provider (get client id and secret):
https://learn.microsoft.com/en-us/entra/external-id/customers/how-to-google-federation-customers
Then we created a user flow and added google as an identity provider and associated the application with the user flow:
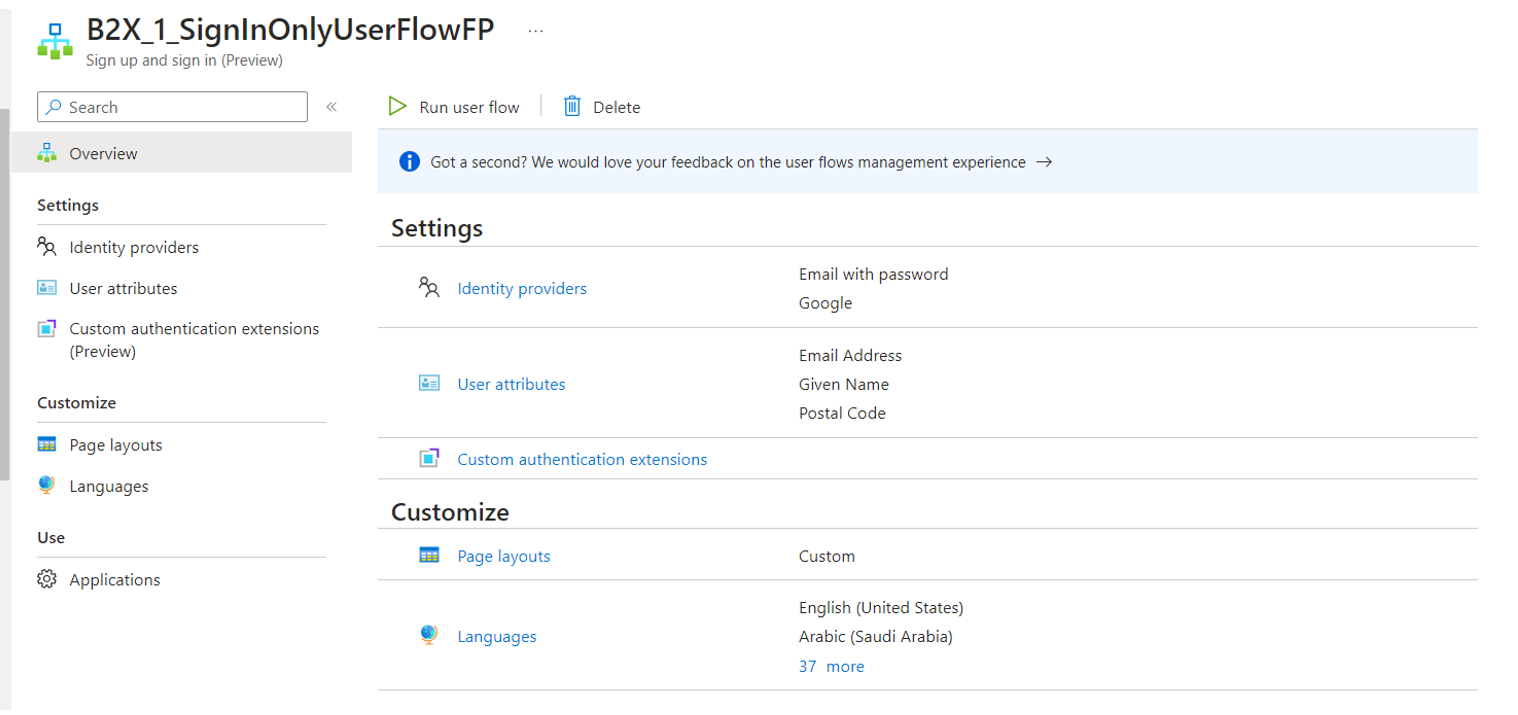
I would greatly appreciate your expertise in providing us with alternatives or a solution for it. If there is any additional information needed, please let me know and I will be happy to provide it promptly.
Thank you very much for your attention. I look forward to hearing from you and working towards a resolution.
Best regards,
Javier Ortega

